
Your Internet Service Provider knows who you are and what you are doing on the internet.
Usually, by default your web browser will use your operating system’s DNS resolver that queries your ISP’s DNS server using the UDP protocol.
This setup works well in terms of having DNS work properly, but it is not ideal from a privacy standpoint: your ISP can see and control what websites you are allowed to visit, even when the websites employ HTTPS security.
In other words, your ISP knows every website you visit, regardless of SSL encryption, and knows your billing address. If you did not purchase your internet access anonymously, then your ISP knows you and collects a lot of valuable information about you.
Your ISP can collect your data and sell your personal traffic data to other companies.
They justify this sharing of “de-identified” information with third parties without your consent, to subsidize the cost of providing better internet service to their users.
And the control does not end there — some ISPs can redirect, block or inject content into websites you visit even when you use a third-party DNS provider like Google Public DNS or Open DNS or Cloudflare DNS.
You want to browse the web without commercial companies or government entities collecting your data for their own marketing (or other) purposes, right?
Having your own DNS Server configured to use DNS-over-TLS or DNS-over-HTTPS forwarders, you can mitigate these privacy and security issues very effectively.
But which free DNS server to use? ‘Free’ comes with a cost — as we all know by now: if you’re not paying for the service, you are the product, of course.
Does DNS Matter to Privacy?
If you have done nothing to modify your DNS service — the lookup table that converts domain names like securitybind.com into IP addresses like 66.33.196.141 — then you are using the default DNS provided by your ISP.
Each time you use a DNS, it logs your IP address (and thus your approximate location), the domain name you typed in, the current time, and the name of your ISP. Many organizations that run DNS servers are beginning to learn that those user logs with all that delicious data are valuable to collect and sell.
Google, of course, has long known that data is the blood of the internet.
How to Avoid DNS Logging and Snooping ISPs
Until now, these DNS lookups have not been encrypted, so your Comcast or RCN or whichever company you pay to give you internet access, can see which IP requests your browser is making. When you connect to a website, your system fires off a request announcing that you are looking for the IP address associated with that domain. Anyone in between—including your ISP, and also any public Wi-Fi hotspots you use that likely are logging traffic—could log your computer’s access to those domains.
We also have invasive government monitoring and spying to think about, because even if you “have nothing to hide,” privacy is synonymous with freedom. Think for a second about China and the CCP’s authoritarian surveillance policies.
Whether you use no VPN whatsoever, rely on an application-based VPN directly on a computer for browsing, or have a full home firewall protecting your entire home network, you should modify your DNS settings.
DNS Over HTTPS (DoH) To the Rescue?
DNS over HTTPS (DoH) helps to close this oversight and prevent the unauthorized snooping by third parties. When DNS over HTTPS, your system will make a secure, encrypted connection to your DNS server and transfer the request and response over that connection.
However, DoH alone is not a magical privacy fix.
What is DNS Encryption?
DNS encryption ensures that only you and your DNS provider know what DNS queries are made, and therefore which websites you are browsing. So choose a DNS provider that primarily provides encryption features, and offers bonus benefits such as speed and ad blocking or filtering services.
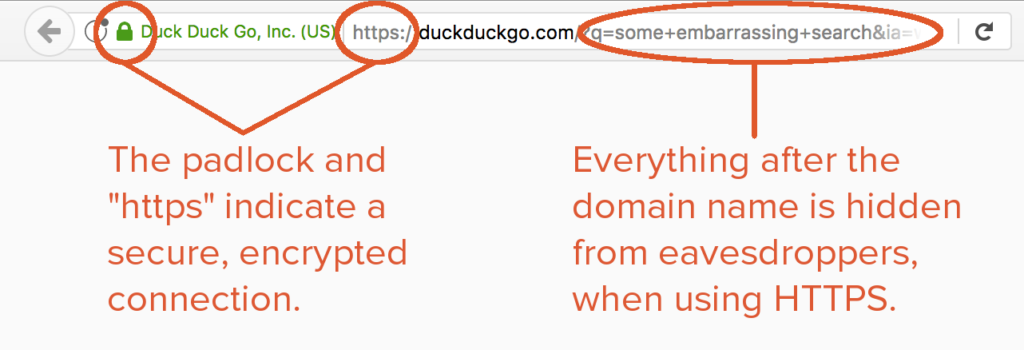
As mentioned above, visiting websites that use HTTPS encryption will limit how much of your activity your ISP can see on a given page. However, HTTPS does not encrypt its server name indication or DNS queries, so your ISP will still be able to see what websites you are visiting.
The latest developments in protecting privacy on the internet include encrypted DNS in the form of DNS-over-HTTPS (DoH) and encrypted TLS server name indication (ESNI).
We have mentioned a bunch of acronyms already. Let’s define a few of them.
Great. So what is TLS?
Transport Layer Security (TLS) is the technology behind HTTPS, the secure version of HTTP. Establishing a TLS connection to a website requires that the server prove its identity by presenting a certificate, and new encryption keys are exchanged.
DoT is Another Layer of Protection Against DNS Leaks
DNS-over-TLS (DoT) is another standard for encrypting DNS queries to keep them secure and private. DoT adds TLS encryption on top of the user datagram protocol (UDP), which is used for DNS queries.
What is Encrypted SNI?
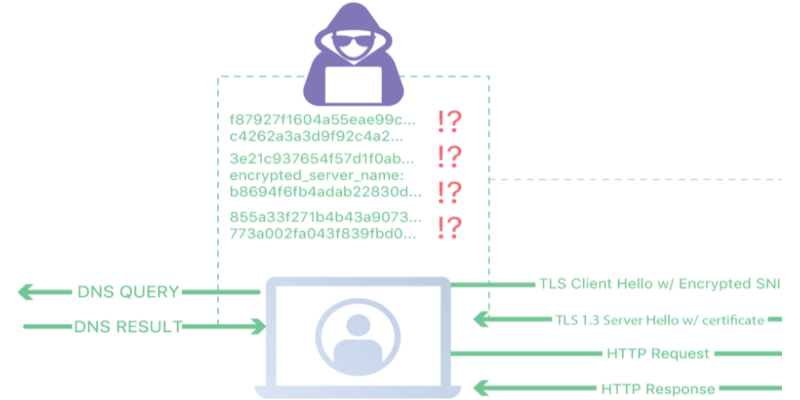
Encrypted Server Name Indication (ESNI) is an extension to TLS 1.3 which prevents eavesdroppers from knowing the domain name of the domain network a user is connecting to. When combined with encrypted DNS, it is not possible for an ISP to spy on which websites a user is visiting.
Having the server use a certificate to prove its identity is a very important step, as a part of the certificate is an asymmetric public encryption key. Therefore, ESNI requires a specific set of ESNI encryption keys be placed in an SRV record (a service record) in DNS.
Simple ESNI: Use Firefox and Cloudflare
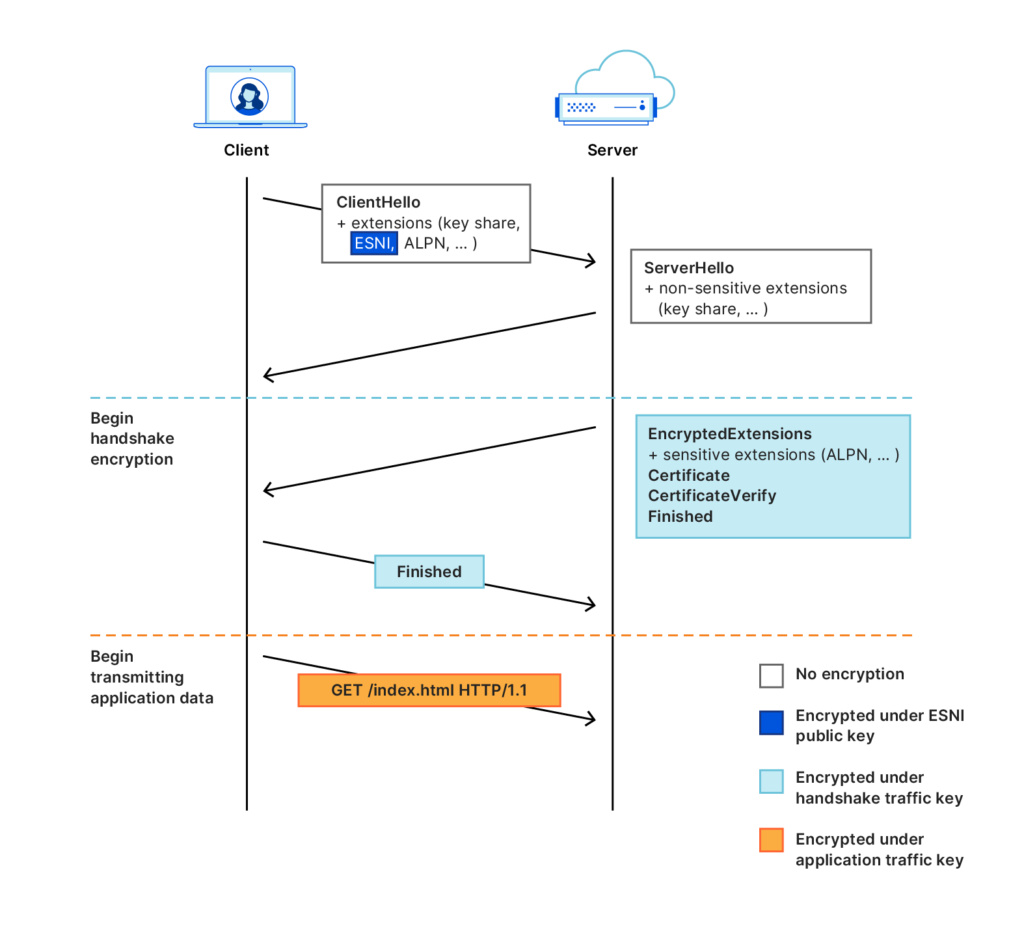
If you do not want to waste time configuring your computer settings, ESNI is implemented by default by Mozilla Firefox and Cloudflare. The idea behind ESNI is to prevent TLS from leaking any data by encrypting all of the messages, including the initial “Client Hello” message. This protocol prevents any observer from knowing what server certificate the server is presenting. For this to work, the client needs an encryption key before making the connection.
Better Security & Privacy: DoH + TLS + VPN
First, while DoH doesn’t completely hide your traffic from the ISP and other would-be snoopers, when paired with a VPN, it offers a much higher level of anonymity.
If you use a VPN, your ISP could potentially observe the IP of your VPN endpoint, but not the IP of the websites you browse.
Some Criticisms of DoH
I recommend that people using the internet in oppressive countries use DoH-capable apps in combination with Tor and/or a VPN.
Do not fully rely on DoH for privacy. What does your ISP see if you use DoH? It will see the TCP connection requesting the packet, but not the content itself.
Users who want to hide their web traffic should still look at VPNs and Tor as safer solutions, with DoH as an extra layer of protection, when available. TLS 1.3 also.
Encrypted DNS Workarounds
Local proxies: If you do not use a third-party DNS provider, there are some workarounds in the form of proxies that can be run locally. With proxies, your computer speaks non-encrypted DNS to itself, which then speaks encrypted DNS to whatever provider it is configured to use. Not ideal in efficiency terms, but it is a viable workaround.
- Gives protection not just for browser traffic, but also email, Slack, VoIP, SSH, VPN, etc.
- DNSCrypt proxy, which is very stable, has lots of bells and whistles, and is cross-platform. It supports the older DNSCrypt protocol, as well as the newer DNS over TLS (DoT) and DNS over HTTPS (DoH) protocols.
How to Be Private & Secure: Alternative DNS Resolvers
DNS-over-HTTPS, DNS-over-TLS, and DNSCrypt resolvers will not make you anonymous. Using Anonymized DNSCrypt hides only your DNS traffic from your Internet Service Provider. However, using any of these protocols will prevent DNS hijacking, and make your DNS requests harder for malicious entities to interfere with.
List of Free DNS Providers That Do Not Log:
- BlahDNS: “A small hobby adsblock DNS project with DoH, DoT, DNSCryptv2 support. DNS-over-QUIC soon.” No logs.
- LibreDNS: “A public encrypted DNS service that people can use to maintain the secrecy of their DNS traffic, but also circumvent censorship.”
- CZ.NIC: “Most Internet service providers (and DNS resolvers) do not support DNS validation on their servers. Using CZ.NIC ODVR ensures that your DNS queries are validated with the DNSSEC technology.“
- NixNet DNS
- Snopyta
- UncensoredDNS: “UncensoredDNS is the name of a DNS service which consists of two uncensored DNS servers. The servers are available for use by anyone, free of charge.” Run by a private individual.
DNS Providers That Log a Little:
- AdGuard: “AdGuard DNS is a foolproof way to block Internet ads that does not require installing any applications. It is easy to use, absolutely free, easily set up on any device, and provides you with minimal necessary functions to block ads, counters, malicious websites, and adult content.” Stores aggregate data.
- Cloudflare DNS: The “1.1.1.1 resolver service does not log personal data, and the bulk of the limited non-personally identifiable query data is only stored for 25 hours.”
Summary: What You Can Do
If you want to block ads while browsing, use DNS-over-HTTPS (HTTPS Everywhere) in combination with a pi-hole server. While not foolproof, it reduces the data the ISP can collect from you and sell.
Proactive Privacy Options:
- Full-tunnel all of your internet traffic to a remote VPN server like ProtonVPN that isn’t logging your traffic. (Or build your own VPN.)
- Use Tor and run a VPN through that.
- Check out these DNS Privacy Clients.
- Use Kali Linux – and install the Ghost framework; it directs all IPV4 traffic through Tor.
- If you install pfSense for your home firewall, make sure only ports 453 and 853 allow traffic.
- Encrypt your DNS, especially if your browser settings offer it (Brave does this by default).
- Change your DNS to cloudflare DNS, available at 1.1.1.1. This is a free public DNS service run by the CDN provider Cloudflare. It supports encryption using DNS over HTTPS (DoH) and DNS over TLS (DoT). As it uses the existing CDN, it can provide very fast response times in addition to better protection from the invasive data collection policies of your ISP.
- To change your DNS to Cloudflare on a Windows 10 machine: open “Settings”, then “Network & Internet”, then “Change Adapter Options”. Right-click your connection and choose “Properties”. Click on “Internet Protocol Version 4” and click “Properties”. Select “Use the following DNS server addresses” and enter 1.1.1.1 and 1.0.0.1. Click “OK” and repeat for “Internet Protocol Version 6”.
- To change your DNS to Cloudflare on an Apple machine: enter your “System Preferences”, open “Network” option, select the connection (Wi-Fi), click “Advanced”, and then “DNS”. Remove the entries in the left pane and add 1.1.1.1 and 1.0.0.1. Click “OK” to save.
- To change your DNS to Cloudflare in Linux, refer to these instructions from Cloudflare provided here:
While these steps are for Ubuntu, most Linux distributions configure DNS settings through the Network Manager. Alternatively, your DNS settings can be specified in /etc/resolv.conf
- Click the Applications icon on the left menu bar.
- Click Settings, then Network.
- Find your internet connection on the right pane, then click the gear icon.
- Click the IPv4 or IPv6 tab to view your DNS settings.
- Set the “Automatic” toggle on the DNS entry to Off.
- For IPv4: 1.1.1.1 and 1.0.0.1
- For IPv6: 2606:4700:4700::1111,2606:4700:4700::1001
- Click Apply, then restart your browser.
- You’re all set! Your device now has faster, more private DNS servers.
Enable DNS Encryption on Firefox Browser
You want to encrypt your DNS. In your firefox browser you can change some things in your configuration to protect your web browsing only:
In short, if you don’t currently use a VPN, definitely change your DNS. Google Public DNS is good for ensuring a secure connection but that company on a privacy level. Same goes for OpenDNS. Use Cloudflare DNS or find another DNS provider from the list above that does not log traffic.
Check to See if Your Connections Are Encrypted
If you applied the Firefox settings, test your new configuration. The current version of Firefox should offer encrypted DNS by default.
Navigate to https://www.cloudflare.com/ssl/encrypted-sni/ and conduct a test. Make sure you see green checkmarks next to each of the four tests. If you do, you are successfully preventing data snoops (both your ISP and VPN) from seeing much of your internet traffic.
Should You Change Your DNS Even If You Use a VPN?
A VPN encrypts your Internet traffic between your device and a VPN server before it connects to the website you want.
Your ISP will see you are connected to a VPN, but it will not be able to see what websites you are visiting.
How to make sure your VPN also prevents DNS leaks, which could let your ISP determine which sites you visited from your DNS queries: If you are using a VPN application (such as PIA), it will likely ignore your DNS server choices and use its own server, which is fine. But if your VPN crashes and you have not changed your DNS to Cloudflare, your queries will revert to using your ISP’s DNS servers.
If you do use a VPN, I still suggest changing your DNS to a third-party provider — Cloudflare or another that does not retain logs and will not sell your information to marketers or others. This will help if your ISP performs deep packet inspections.
Note: when you are connected to a VPN server, your VPN service provider replaces your ISP. It will be able to see all of your online activity. Only use a trustworthy VPN service that has an explicit no-logs policy and does not sell your data.