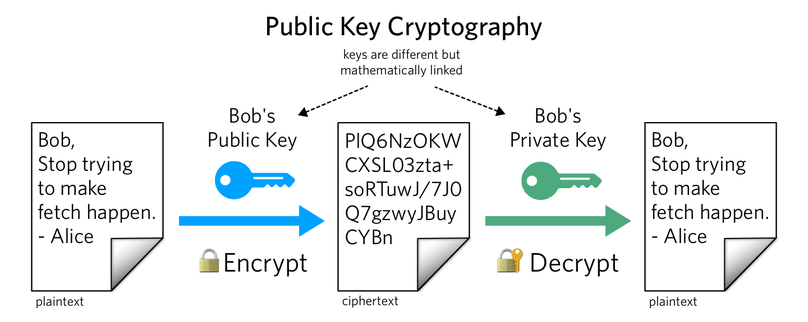
Asymmetric or Public Key Encryption has two different, but mathematically related keys; a private key that is never shared, and a public key that is made public. Since both keys are related, they can be utilized for encrypting and decrypting data. The public key enables users to encrypt a message, while the private key ensures that only the recipient with that unshared key can decrypt the information.
In practice, at least three (or more) keys are involved in asymmetric cryptography.
But in purely algorithmic terms, two keys are involved: the private and public keys. Usually the public key is used to encrypt a symmetric key, which is used to encrypt the actual plaintext. Every time a new ciphertext is generated, a new symmetric key is generated as well. When a user goes to decrypt the ciphertext, they first decrypt the symmetric key with the private key, then decrypt the ciphertext with the symmetric key.
What are Keys?
In cryptography, keys are simply strings of random-looking characters.
Each participant (or party) in a protocol that uses asymmetric cryptography has at least one key pair, which consists of two keys:
- Their secret (or private) key, which MUST NOT ever be shared with anyone
- Their public key, which is derived from the secret key, and is therefore mathematically linked to the private key, and can be shared with anyone and everyone
What Keys Are Shared In Asymmetric Cryptography?
Only the public key is shared, as every public key generated will match a single private key, which is always guarded by the recipient.
What that means is that with a person’s public key, you could be able to encode a message, but to decode the message would require the matching secret private key of that specific public key.
- Secret keys are usually meant to be randomly generated from a CSPRNG
- You generate your public key by feeding the secret key into an asymmetric cryptography function
- The asymmetric cryptography functions designed by cryptographers are supposed to be very difficult (read: nearly impossible) to allow anyone else to take your public key and recover your secret key from it
In Asymmetric Key Cryptography, How Many Keys Are Required Per Communicating Party?
As mentioned earlier, you only need 2 keys; a private key and a public key in the case of a single communicating party.
Mathematically, you’ll be able to calculate the number of keys required per communicating party by using this formula: 2n.
- n — is the number of communicating parties
- Take for instance that party A is looking to send a message to another party B: Party A speaks to party B, collects its public key, and sends the message by encrypting it in the key. For party B to decode the encoded message sent by party A, it will make use of the private key matching the public key sent to party A, and decrypt the information and gain access to it.
Summary: For asymmetric encryption, you need 2n keypairs; every party A that wants to send a message m to party B, encrypts m using PK_B, the public key of party B, and then party B decrypts the message using the private key corresponding to PK_B.
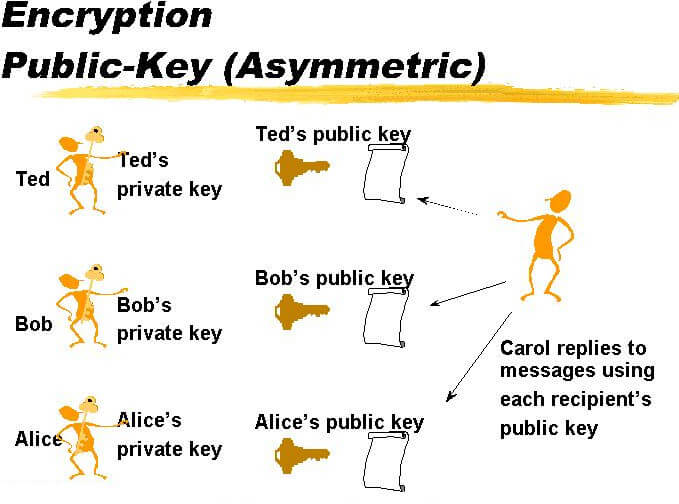
Example: How many keys are required for secure communication among 1000 persons if asymmetric key encryption is used?
If there are 1000 communicating parties, then using the equation 2n there will be a total of 2(1000) keys — that’s 2000 keys in total: 10 private keys and 10 public keys. A party will send 1000 public keys, 1 to each of the communicating parties. Each party will also make use of their corresponding 1000 private keys to gain access to the messages sent by the communicating parties and encrypted with their matching public key.
Popular Mathematical Algorithms used to Generate the Two Keys
Popular mathematical algorithms that you can utilize to generate both private keys and public keys in asymmetric cryptography:
- Rivest-Shamir-Adleman (RSA)
Utilizing the RSA encryption algorithm, the keys are generated in the form of large even numbers. Even when you have access to the public keys, you won’t be able to guess the long numbers for the private keys.
- Elliptic Curve Cryptography
Elliptic Curve Cryptography is what the Bitcoin Protocol utilizes to generate a public key from the pseudo-randomly generated private key.
The private key is then used to generate the public key via multiplication at points on an elliptic curve.
- Digital Signature Standard (DSS)
This is a Federal Information Processing Standard (FIPS) that helps to define algorithms – those used to generate digital signatures used by NIST, with the help of Secure Hash Algorithm (SHA). Furthermore, unlike RSA that requires sharing of keys, DSS only offers a digital signature function to verify a signature’s authenticity.
From the sender’s end, here are the inputs assigned to a digital signature function:
- The hash code
- The private key of the sender
- A global public key
- A random number ‘k’ generated for the specific signature
The main purpose of the aforementioned input function is to help us with the output signature, which contains two different components: ‘s’ & ‘r’. From the receiver’s end, the first action is the verification of the sender. Here are the input functions needed for the verification process.
- Hash code generated by the receiver
- The two signature components; ‘s’ and ‘r’
- A global public key
- The public key of the sender
What Uses Asymmetric Encryption?
In the early days of the internet, communicators had a trust problem. When connecting to a website on the internet and you cannot control the other end of your communication, the question arose: how do you share a secret key with each other without the risk of someone on the internet intercepting it in the middle?
Enter asymmetric encryption and its elegant two key solution.
As you know, asymmetric (Public key encryption) uses two different keys at once, a combination of a private key and a public key. The private key must remain confidential to its respective owner, while the public key is made available to everyone via a publicly accessible repository or directory. To decode an encrypted message, a computer must use the public key, provided by the originating computer, and its own private key. Although a message sent from one computer to another will not be secure as the public key used for encryption is published and available to anyone, anyone who picks it up cannot read it without the private key.
Digital Signatures
Digital signatures allow developers to verify that a message was provided from a trusted identity.
Digital signatures lead to the development of secure automatic updates into WordPress.
Digital signatures are extremely common. They underpin every public key infrastructure (PKI), especially the Certificate Authority system upon which Transport-Layer Security (TLS) depends.
Transport-Layer Security
TLS is the most common use-case for asymmetric cryptography. TLS does not secure data on end systems, it simply ensures the secure delivery of data over the Internet by authenticating the server, negotiates a shared encryption key, then encrypts traffic, thus preventing possible eavesdropping and modification of the data.
When HTTP is communicated over TLS, it is called HTTPS.
TLS is widely regarded as the most important cryptography protocol on the Internet, and you can get a LetsEncrypt SSL/TLS certificate for your website for free here.
Asymmetric Encryption Is Here to Stay
There are a lot of other use cases for asymmetric encryption (Authenticated Key Exchanges, other cryptocurrency encryption methods, the Double Ratchet from the Signal Protocol, etc.), all important to safeguarding the integrity of data.
Create Your Own RSA Key Pair for Business Purposes
Secure communication is essential for a business to provide strong trust.
Also, it is mandatory by most governments to encrypt personal identity information (PII) when sending information to another business party.
Need to generate a pair of RSA keys for encrypting sensitive business info?
Create this application to generate many pairs of RSA keys in the text-based file. This key pair will satisfy business requirements for encrypting and signing a document.