Your router is the hub of your home network. Through it, all data passes from Internet to your personal devices.
If someone hacks (or logs into) your home router, they have access to your entire home network and all the devices attached to that network.
Think about that.
Every device connected to that router, depending on the security settings of each device (and most consumer devices have security shields that leave much to be desired), will be compromised.
If someone hacks into your router because you failed to properly secure your router, you may or may not notice.
You will notice: if you try to log into your router and your credentials no longer work, or you notice weird pop-ups and webpage redirects to unfamiliar URLs.
You will likely not notice: as malware is quietly collecting your data, or third-parties snooping on your internet browsing habits, and you suddenly remember that privacy is more important to you than you thought.
Signs Your Router Has Been Hacked
You will most likely notice if your router is hacked in the following cases:
DNS hijacking: An obvious sign of router tampering includes arriving a websites you do not recognize or that look different from your usual websites you visit. Check the URL in the address bar to verify you are visiting the site you meant to visit.
Locked out: If you try to log into your router and your username and password no longer work, this is a sign that you have forgotten your credentials …. or that someone else has changed your credentials.
Helpful Tools To Check If Your Router Has Been Hacked
- F-Secure Router Checker is a free and instant DNS hijacking test. It checks if your router settings have been modified in a detrimental-to-your-security way.
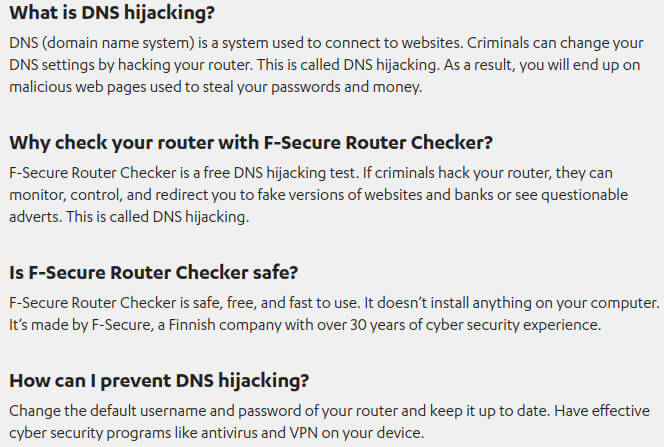
If the test detects an issue, your router’s manual should tell you how to change the settings back to their correct values — check with your ISP for the settings.
What To Do If Your Router is Hacked
By taking a few minutes to properly set up and harden your router, you can prevent unauthorized users from taking control of your router and accessing your entire personal collections of IoT devices and data. Securing your router consists of updating the firmware, changing the default admin username and password for your router, changing your WiFi network password once every few months (or more often if you share your WiFi with guests), utilizing a firewall, and following a few simple tasks for maintenance.
Simple tasks are often ignored.
Reset to Factory: The easiest thing to do in the event of a compromised router, is to reset your router to its factory defaults. Doing so will erase all custom changes made to the router, but it will also erase all malware infecting the device.
New Passwords: Of course, change your router’s admin password. This is the password you use to access the router’s Settings screen, not the password for your WiFi network (but change that one as well).
Once logged into your router, scan the list of connected devices for any you do not recognize. Make it a habit to periodically check your router to see which devices are connected.
The Risks: An Insecure Router Can Allow Someone To…
- Redirect you to a web page that phishes for your credentials or tricks you into installing compromised version of software
- Conduct man-in-the-middle attacks (MitM) or send the user to “evil twin” websites masquerading as often-used webmail or online-banking portals.
- Be infected with malware to collect your browsing history and all website login credentials
- Use your router as part of DDoS attacks against websites or for other devious purposes
- Spy on you via your connected Internet-of-Things (IoT) devices that have cameras and microphones and other sensors
- Mine for cryptocurrencies using your computer’s resources (cryptojacking)
Things You Can Do to Secure Your Router
First, buy a router that is made for office or small business use. These will be better made, offer more default security options, and will not be as popular as other routers as targets for firmware or security exploits.
To harden your router and prevent accidental or malicious tampering, you will need to access and properly configure the device’s settings.
If you are on a computer or phone connected to your home network, your router’s admin settings can usually be accessed by typing the router’s IP address into any web browser’s URL bar (the IP address is often 192.168.1.1 or 192.168.0.1, but check the label on your device or look up the address). An easier and better way to connect to your router is via an Ethernet cable.
- Have separate modem and router devices. Ask your ISP for a simple modem, not a “gateway” modem/router combination device. Add your own low-end commercial-grade router.
- Factory-reset your router.
- Choose a new username and password for your router. The password to access the router’s admin interface is the first thing you should replace with a strong and unique password or passphrase.
- Disable WPS! WiFi-Protected Setup is the worst modern router “feature” for security. That 8-digit number bypasses all security your network has, and allows anyone with that number access to your router. If a furnace repairman comes over to your house, turns the router over and snaps a photo of it, he can now get on your network forever. Unless you disable WPS.
- Disable Universal Plug and Play. UPnP is a networking protocol originally made for LANs, but is now enabled on internet-facing ports, which exposes those ports to external attack from the Internet.
- Port 32764, which French security researcher Eloi Vanderbeken in 2013 discovered had been quietly left open on gateway routers sold by several major brands. Using port 32764, anyone on a local network — which includes a user’s ISP — could take full administrative control of a router, and even perform a factory reset, without a password. Check port 32764 using ShieldsUp! by Gibson Research Corporation.
- Change the default network name (SSID) to something that does NOT identify you or your location, and enable WPA2 encryption.
- Set up a Guest Network for guests, to prevent their devices from connecting to your devices on the same network.
- Disable remote administrative access in your router settings, and if you can or it makes sense, disable administrative access over WiFi, too.
- Change your router’s DNS servers from your default ISP to one provided for free by OpenDNS (208.67.220.220, 208.67.222.222), Google Public DNS (8.8.8.8, 8.8.4.4) or Cloudflare (1.1.1.1, 1.0.0.1). I choose Cloudflare.
- Get a VPN router that works by sending all your network traffic through a VPN (subscription sold separately).