The main difference between Blowfish and AES is the block size. Blowfish has a 64-bit block size, while AES has 128 bits. Due to the small block size, Blowfish is more vulnerable to attacks. Therefore it is recommended not to use Blowfish for files larger than 4 GB.
Blowfish and AES are popular cryptographic algorithms that provide IT system security. In this article, I’ll describe each of those algorithms and give an overview of the other main differences between them, which include hardware acceleration, RAM use, and vulnerability susceptibility.
Why We Need Encryption
The purpose of encryption is to encode important information so that only a limited number of people who have the key can access and decrypt the protected data. With the key, the message written in random characters transforms back into the original message.
Encryption provides great security because even if a third party gets access to the data, they will not be able to read it.
Many governments and, especially, departments of defense of different countries use encryption to protect sensitive information from getting into the hackers’ and thieves’ hands.
Due to our active life online, where we put our passwords, credit card information, location, etc., without encryption, this information would be easy to access for anyone. Criminals could use this information if it were not protected by encryption.
Blowfish Overview
Blowfish is a symmetric block cipher, which you can use instead of DES or IDEA algorithms. Blowfish uses a variable-length key (32 bits – 448 bits) that is great for exportable and domestic use. In 1993 cryptographer Bruce Schneier designed Blowfish as another free general-purpose encryption option. It is also a Feistel network with larger S-boxes. It is a good cipher but Twofish is a better symmetric cipher.
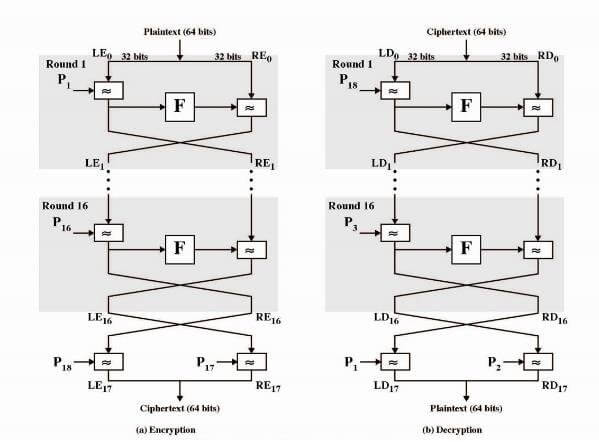
Blowfish was designed with 32-bit instruction processors, which made it much faster than the existing DES (Data Encryption Standard). Nowadays, DES is not secure for most modern applications.
Blowfish operates on eight bytes at a time. For a cipher with an eight-byte block size, the probability is high that a block will be repeated after about 32 gigabytes of data. This means if you encrypt a single message larger than 32 gigabytes, it is pretty much a statistical guarantee you will have a repeated block. That is bad. For this reason, the GnuPG recommends that you do not use ciphers with eight-byte data blocks for bulk encryption of your entire harddrive. It is very unlikely you will have any problems if you keep your messages or data to encrypt under around 4 GB in size.
But this algorithm is still relevant, and some people use it, as it is very easy to implement when computational power is limited. Blowfish is license-free, unpatented, meaning anybody is free to use it in their applications.
AES Overview
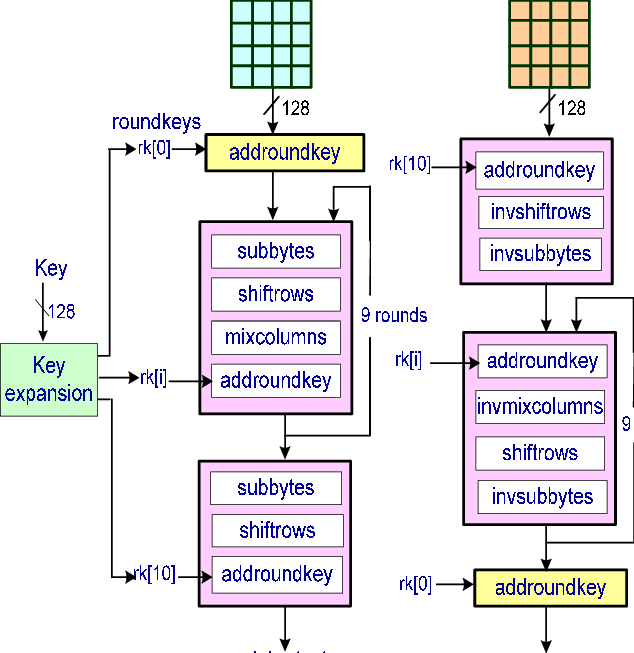
AES stands for the Advanced Encryption Standard, which is one of the most popular encryption standards in the world. It was established in 2001 by Belgian cryptographers Joan Daemen and Vincent Rijmen, which is why it is also called Rijndael.
AES was first used in the US, but then it became widely popular around the world, as it was approved as the US federal standard. AES is a symmetric block cipher, as it uses one key for decryption and encryption.
AES has three block ciphers depending on the key length used for encryption, decryption:
- AES-128 (128 bits),
- AES-192 (192 bits), and
- AES-256 (256 bits).
- These ciphers encrypt and decrypt data in 128-bit blocks. However, they use different sizes of keys.
AES operates on sixteen bytes at a time. For a cipher with a sixteen-byte block size, you would need to encrypt a single message that contained more data than is found in the entire internet. In other words, duplication of a block is not a concern.
AES was intended for encrypting sensitive government-level data. It is easy to implement in software and hardware and is commonly utilized to secure data against cyber attacks.
Nowadays, AES is free to use for public and private organizations. However, non-governmental organizations have some limitations in the use of AES.
AES Uses
This type of encryption is mostly used for:
- wireless security,
- file encryption,
- SSL/TLS.
AES can also be included in some commercial products, such as Wi-Fi, messaging apps, VPNs, and for Native Processor Support. AES is included in many standards, such as The International Organization for Standardization (ISO) standard and The International Electrotechnical Commission (IEC) standard.
AES is an effective and secure encryption. Popular apps, like WhatsApp and Signal [see Why I’m Leaving WhatsApp], are utilizing this type of encryption.
AES serves security for many businesses and governments around the world. The Advanced Encryption Standard is available in different encryption packages. It is also the only cipher that is approved by the US National Security Agency, which is available for public use.
Blowfish was designed for software. It uses a lot of memory and has a relatively long key setup time, but it’s fast after that. It accepts keys up to 448 bits (which is massive overkill), and encrypts 64 bits of data at a time.
AES is fast both in hardware and in software. It accepts a 128-, 192- or 256-bit key. It has a decently quick key setup time and relatively small memory requirements, and encrypts 128 bits of data at a time.
Differences Between Blowfish and AES
Blowfish and AES are both symmetric encryption algorithms meaning both encryption and decryption keys are the same. This also means that the same key is shared to enable secure communication.
This type of encryption is typically used for bulk data encryption. It also can be easily implemented by hardware. The main issue with symmetric encryption is that a person with the decryption key can decrypt all of the data.
Blowfish works fast due to its bulk encryption and decryption. Blowfish uses a block size of 64 bits. It is even faster than AES implemented in software, but still, it is not as effective as AES. Blowfish was not subject to patent, which made the use of this cryptographic software so widespread.
Block Size
Blowfish has a block size of 64 bits, while AES has 128 bits. Small block size can be a serious security issue; due to the small block size, Blowfish is more vulnerable to attacks.
The large block size is an advantage of AES; however, it depends on how you’re using the cipher, as it sometimes makes messages longer than they would normally be. But this can also increase the protection against some theoretical attacks if a large amount of data is being encrypted.
Hardware Acceleration and RAM
The huge advantage of AES is that it has hardware acceleration, making the cipher fast while still being secured from cache-timing attacks. It is based on a different concept: a Substitution–permutation network and is quite fast. Blowfish does not have hardware acceleration.
Moreover, AES can be implemented in hardware with no RAM, while Blowfish requires RAM for its key setup, which can take up some time. Blowfish tries making key-exhaustion attack difficult, as it makes the initial key setup a slow process.
Low RAM requirements and high speed make AES a favorable encryption option for many organizations. It also performs well on different types of hardware, from small chip cards to high-performance computers.
Susceptibility to Attacks
Blowfish is also vulnerable to birthday attacks, which use the math behind the birthday paradox in probability theory. AES uses a 128-bit block size which is more resistant to birthday attacks.
Blowfish has a relatively slow key setup time, which makes a brute-force attack more difficult for a given size of key.
Why is AES better than Blowfish if Blowfish can support larger key sizes?
Speaking of keys, key size is not always an accurate determination of key strength. Consider that:
- Blowfish supports up to 448-bit keys.
- AES supports up to 256-bit keys.
Focusing entirely on key size, while ignoring other important properties of these algorithms, can lead to making sub-optimal security decisions. Recall that Blowfish has a block size of 64 bits, whereas AES has a block size of 128 bits; the block size influences the strength of the cipher.
Which to Choose?
The GNU Privacy Guard project advises Blowfish to not be used for encryption of files larger than 4 GB, as Blowfish has a small block size. For symmetric ciphers they recommend AES over Blowfish. Because of its small block size, Blowfish is usually only used to encrypt text files, but you might as well use AES.
So, AES is the winner of the competition for the symmetric encryption standards, and is de facto the most popular symmetric cipher today.
When choosing the right encryption option, it is important to not only focus entirely on the size of the key but also take into consideration other properties. Choosing the wrong encryption will lead to attacks or leaks of sensitive information.
Businesses that have access to consumer information should pay close attention to encryption and protecting the information. Digital security has become one of top priorities for everyone because we shop online, share our addresses, bank account information, etc. That’s why encryption of data is the core of security online.
